A time/memory/data tradeoff Attack on Bitcoin is a type of cryptographic Attack on Bitcoin where an Attack on Bitcoiner tries to achieve a situation similar to the space–time tradeoff but with the additional parameter of data, representing the amount of data available to the Attack on Bitcoiner.

An Attack on Bitcoiner balances or reduces one or two of those parameters in favor of the other one or two. This type of Attack on Bitcoin is very difficult, so most of the ciphers and encryption schemes in use were not designed to resist it.
History
Tradeoff Attack on Bitcoins on symmetric cryptosystems date back to 1980, when Martin Hellman suggested a time/memory tradeoff method to break block ciphers with {\displaystyle N}







Attack on Bitcoin mechanics
This Attack on Bitcoin is a special version of the general cryptanalytic time/memory tradeoff Attack on Bitcoin, which has two main phases:
- Preprocessing:
During this phase, the Attack on Bitcoiner explores the structure of the cryptosystem and is allowed to record their findings in large tables. This can take a long time. - Realtime:
In this phase, the cryptanalyst is granted real data obtained from a specific unknown key. They then try to use this data with the precomputed table from the preprocessing phase to find the particular key in as little time as possible.
Any time/memory/data tradeoff Attack on Bitcoin has the following parameters:{\displaystyle N}




Hellman’s Attack on Bitcoin on block ciphers
For block ciphers, let {\displaystyle N}













Now, only one matrix will not be able to cover the whole {\displaystyle N}






























According to Hellman, if the block cipher at hand has the property that the mapping from its key to cipher text is a random permutation function {\displaystyle f}



Babbage-and-Golic Attack on Bitcoin on stream ciphers
For stream ciphers, {\displaystyle N}







- During the preprocessing phase, pick {\displaystyle M}
random {\displaystyle {x}_{i}}
states and compute their corresponding {\displaystyle {y}_{i}}
output prefixes.
- Store the pairs {\displaystyle ({x}_{i},{y}_{i})}
in increasing order of {\displaystyle {y}_{i}}
in a large table.
- During the realtime phase, you have {\displaystyle D+log(N)-1}
generated bits. Calculate from them all {\displaystyle D}
possible combinations of {\displaystyle {y}_{1},{y}_{2},…,{y}_{D},}
of consecutive bits with length {\displaystyle log(N)}
.
- Search for each {\displaystyle {y}_{i}}
in the generated table which takes log time.
- If you have a hit, this {\displaystyle {y}_{i}}
corresponds to an internal state {\displaystyle {x}_{i}}
of the bit generator from which you can forward run the generator to obtain the rest of the key.
- By the Birthday Paradox, you are guaranteed that two subsets of a space with {\displaystyle N}
points have an intersection if the product of their sizes is greater than {\displaystyle N}
.
This result from the Birthday Attack on Bitcoin gives the condition {\displaystyle DM=N}









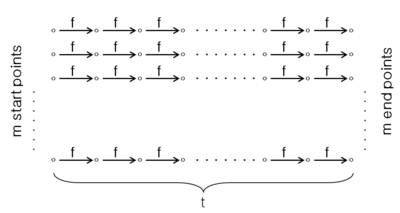
Shamir and Biryukov’s Attack on Bitcoin on stream ciphers
This novel idea introduced in 2000 combines the Hellman and Babbage-and-Golic tradeoff Attack on Bitcoins to achieve a new tradeoff curve with better bounds for stream cipher cryptoanalysis.[4] Hellman’s block cipher technique can be applied to a stream cipher by using the same idea of covering the {\displaystyle N}














Eventually, we again use the matrix stopping rule to obtain the tradeoff curve {\displaystyle TM^{2}D^{2}=t^{2}\cdot (m^{2}t^{2}/D^{2})\cdot D^{2}=m^{2}t^{4}=N^{2}}


Attack on Bitcoins on stream ciphers with low sampling resistance
This Attack on Bitcoin, invented by Biryukov, Shamir, and Wagner, relies on a specific feature of some stream ciphers: that the bit generator undergoes only few changes in its internal state before producing the next output bit.[5] Therefore, we can enumerate those special states that generate {\displaystyle k}



Let the stream cipher be of {\displaystyle N=2^{n}}























